TrueRNG v3 – Hardware Random Number Generator
Improvements
The TrueRNG v3 is our next generation Hardware Random Number Generator. We have optimized the design to increase the speed to over 400 kbits/second while improving the whitener and entropy mixing algorithm.
The new entropy mixing algorithm takes in 20 bits of entropy and outputs 8 bit to ensure that maximum entropy is maintained. The algorithm uses multiplication in a galois field similar to a cyclic redundancy check to mix the ADC inputs thoroughly while spreading the entropy evenly across all bits.
The previous version (TrueRNGv2) has some very minor bias (<1e-6) when averaged over 100’s of megabytes which has no significant effect for cryptographic use but has caused some questions when it shows up in long statistical tests. The new TrueRNG v3 algorithm uses a more advanced whitening technique to reduce the bias below levels where it can be measured reliably.
Overview
The True RNG provides a steady stream of random numbers through a USB CDC serial port. The random number data can then be used to fill the entropy pool of an operating system, or used directly in a custom application. The TrueRNG is ideal for Security related applications (SSH, SSL, GPG), Gaming (dice,cards), Statistical Sampling and simulations.
Theory of Operation
The TrueRNG Hardware Random Number Generator uses the avalanche effect in a semiconductor junction to generate true random numbers. The avalanche effect has long been used for generation of random number / noise and is a time-tested and proven random noise source. The semiconductor junction is biased to 12 volts using a boost voltage regulator (since USB only supplies 5V), amplified, then digitized at high-speed. The digitized data is selected and whitened internal to the TrueRNG and sent over the USB port with more than 400 kilobits/second of throughput.
The Problem
An increasing number of computer software packages rely heavily on the availability of a source of random numbers. In some cases, these software packages require a large amount of random numbers for things such as SSH, SSL, GPG, etc. In the Linux operating system, the kernel keeps a small entropy pool (4 kiloBytes) that is used by applications. If this pool is depleted then the kernel will block causing a delay until the kernel can provide the requested random numbers. The Linux kernel can only slowly replenish the pool using keyboard timings, mouse movements, interrupt, and IDE timings because of the lack of a high-speed source of quality random numbers.
The Solution
A true hardware random number generator (HWRNG) will provide a high-speed source of entropy to the Linux kernel which minimizes blocking and delays while maintaining security. Most of the HWRNG that are available offer high security at a high cost. If you are a bank, financial institution, or run a huge e-commerce site, it may be worthwhile to invest several thousand dollars in a HWRNG, but this this not economical for most individuals and small enterprises. The TrueRNG is a low-cost USB Hardware Random Number Generator that provides more than 400 kilobits/second of true random numbers. This will refill the Linux entropy pool almost instantly and eliminate unnecessary blocking / delays.
Without TrueRNG
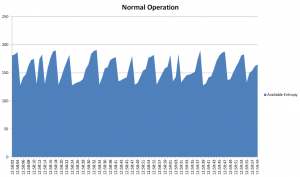 This is what the normal entropy level looks like on a light use Linux server, without TrueRNG.
This is what the normal entropy level looks like on a light use Linux server, without TrueRNG.
With TrueRNG
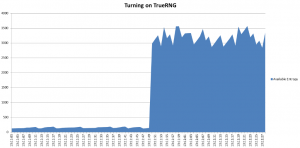 Having the entropy pool filled on a Linux machine using a TrueRNG with the rng-tools package. Notice the immediate gain in available entropy.
Having the entropy pool filled on a Linux machine using a TrueRNG with the rng-tools package. Notice the immediate gain in available entropy.
 Instant entropy recovery with TrueRNG + rng-tools on Linux. Entropy pool was artificially emptied to show recovery rate, Normal tasks such as SSH/Encryption didn’t create enough visible notice to graph. This was with a 1s sampling resolution, but the recovery was much faster than that.
Instant entropy recovery with TrueRNG + rng-tools on Linux. Entropy pool was artificially emptied to show recovery rate, Normal tasks such as SSH/Encryption didn’t create enough visible notice to graph. This was with a 1s sampling resolution, but the recovery was much faster than that. Features
- High Output Speed: >400 kilobits / second
- Internal Whitening
- Native Windows (XP/8/8.1/10) and Linux Support (CDC Virtual Serial Port)
- Passes all the industry standard tests (Dieharder, ENT, Rngtest, etc.)
- Low power <= 20 mA
- Compatible with embedded environments such as Beaglebone, Raspberry PI, and UDOO
Applications
- Security (SSH,SSL, GPG, etc).
- Gaming Servers (Lottery, Dice Roller, Coin Flipper, Playing Cards)
- Statistical Sampling
- Simulations
- Global Consciousness Project
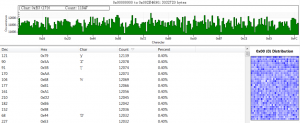
Bitmap Analysis

Showing the random stream as a bitmap shows no visible patterns like a pseudo random number generator will
Character Distribution of 3 MB file
A Character distribution plot of a 3 MB stream captures shows that the min/max of character occurrences are between 0.38% and 0.40%
100 Mb File Entropy Analysis
Linux command: ent random.dat
(Results may vary between runs)
Entropy = 7.999998 bits per byte. Optimum compression would reduce the size of this 106760304 byte file by 0 percent. Chi square distribution for 106760304 samples is 260.12, and randomly would exceed this value 50.00 percent of the times. Arithmetic mean value of data bytes is 127.4937 (127.5 = random). Monte Carlo value for Pi is 3.141909600 (error 0.01 percent). Serial correlation coefficient is 0.000026 (totally uncorrelated = 0.0).* File captured in Linux using dd, entropy analysis done by package ent
What Not To Do
There have been some programmers who have developed software and techniques to quickly fill the entropy pool with pseudorandom numbers. Although this may solve the blocking issue, it unacceptably degrades security by causing applications to use potentially deducible random numbers. This may allow the “bad guy” to gain access to your protected information.
Requirements
- Linux — The USB Driver is included in most Linux Distributions. There is currently application support under rng-tools for Linux to fill the kernel’s entropy pool with data from TrueRNG.
- Windows — We provide a signed driver which allows the device to be used in windows with custom applications.
- OSX — Support is minimal, driver is included in OSX but a custom application or port of rngd would be needed to fill the system’s entropy pool
- USB 2.0
Tools | App Notes | Code Samples
- Windows C++ Class (User Contributed source code)
- RNGCapture – a Console Windows app to capture data (updated 9/25/15)
- Code to use TrueRNG in MatLab (User Contributed / Externally hosted)
Documentation and Support
- TrueRNG Install Guide (Windows | Linux | rng-tools )
- FAQ – Frequently Asked Questions
- Support Forums
Downloads
- Linux UDEV rules and Python Tests (for normal Linux distros) (updated 1/12/2021)
- [Note about unconfirmed Ubuntu 15.04 possible issues here,]
- Linux MDEV rules (for busybox systems)
- CentOS 5/6 easy install script (User Contributed) (updated with Fedora based rules)
- Signed Windows INF Driver
- Sample 1MB file